Welcome back to part 3 of my Top 5 Aviatrix Security Features.
If you missed them, you’ll find parts 1 and 2 here below:
But let’s jump into today’s subject, ThreatIQ and ThreatGuard.
Ever since the first 2 IT systems were connected together, forming what we nowadays refer to as the “network”, we’ve been collectively concerned about people doing things they’re not supposed to be doing on the “network”.
You can think of Threat IQ as the kid at school who would always see what mischief is happening and tell the teacher. ThreatGuard is simply giving that kid the authority to tell the others to stop their mischief. The big difference here is that ThreatGuard doesn’t get beaten up by the other kids.
Seriously, though, your digital assets are targets for all sorts of bad actors out there. Threats come not only from outside the company but also from within.
Why should Cloud customers care?
Cloud customers are unaware of data exfiltration and botnet operations due to compromised hosts.

On top of that, internet access is everywhere in the cloud and on by default for some CSPs.
ThreatIQ and ThreatGuard protect businesses from security risks associated with data exfiltration, crypto mining, TOR, DDoS, and more.
Think about one particular scenario: Cloud computing has put high-powered computing in the hands of anyone with a credit card. This compute-power is great for powering your business, but the temptation to leverage this power for bitcoin mining or other malicious use cases is sadly common. You don’t want to be footing the bill for those costs.

And bitcoin is only one part of it. Accessing ToR servers or other untrustworthy sources can have catastrophic consequences for your business.
In short, there are a lot of reasons to be vigilant.
How do I know what a malicious actor looks like?
Well, they don’t look like this:

Malicious actors are just IP addresses as far as the network is concerned. The network doesn’t care who is sitting at the other end of the IP address:
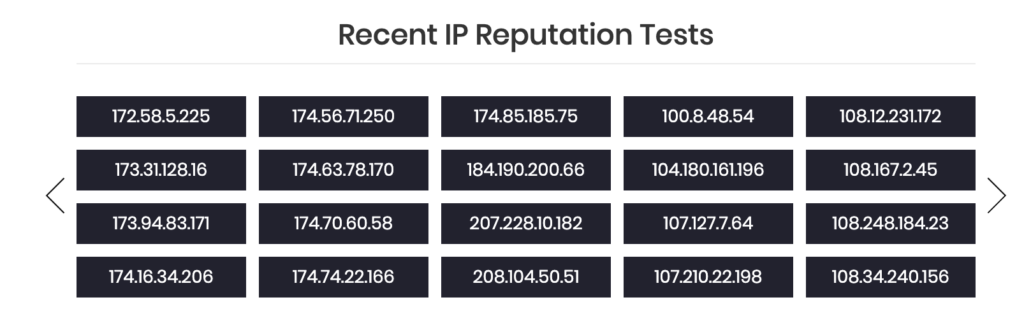
IP Addresses have reputations?
They sure do.
And there are many cybersecurity companies out there building databases of known bad guys (IP addresses).
Have a look here to find out more, rather than me parroting the facts:
https://www.ipqualityscore.com/ip-reputation-check
But I have all sorts of firewalls and security boxes that just take care of that for me.
Funneling traffic through choke points or 3rd party services is inefficient and ineffective.
We believe strongly in security in layers, and also believe that such threats must be cut off as close to the source of the threat as possible. What is needed is a distributed enforcement model, not centralized point solutions – which have their place, just not here.
So, how does Aviatrix help?
Aviatrix has an advantage that no other solution has. Can you tell from the graphic below?
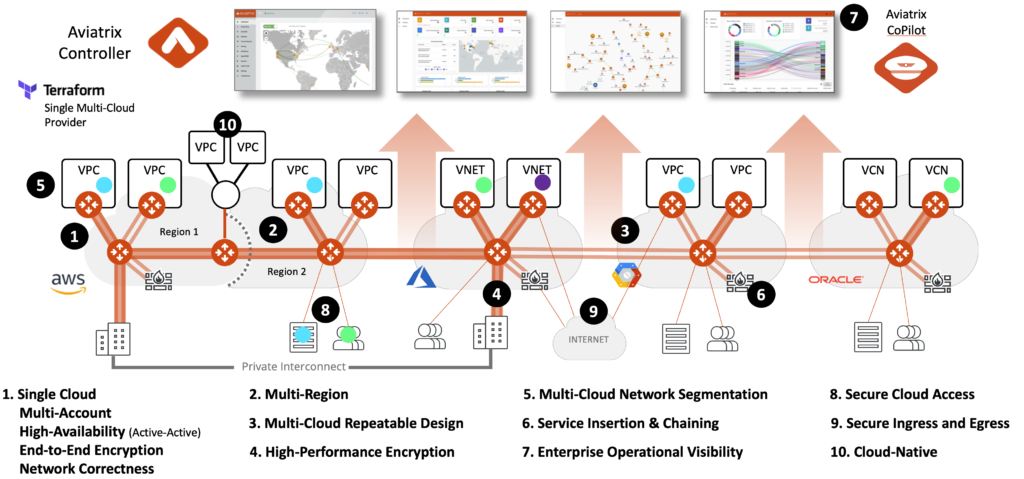
We are in the end-to-end data path and collect all Netflow information as traffic moves around the network.
This is critical to understand, as we now have a wealth of information to leverage for intelligent decisions.
ThreatIQ leverages this Netflow information and cross-references it with third-party malicious actor databases.
ThreatIQ, through CoPilot, will then alert you on these events:
ThreatGuard takes ThreatIQ intelligence and makes it actionable:
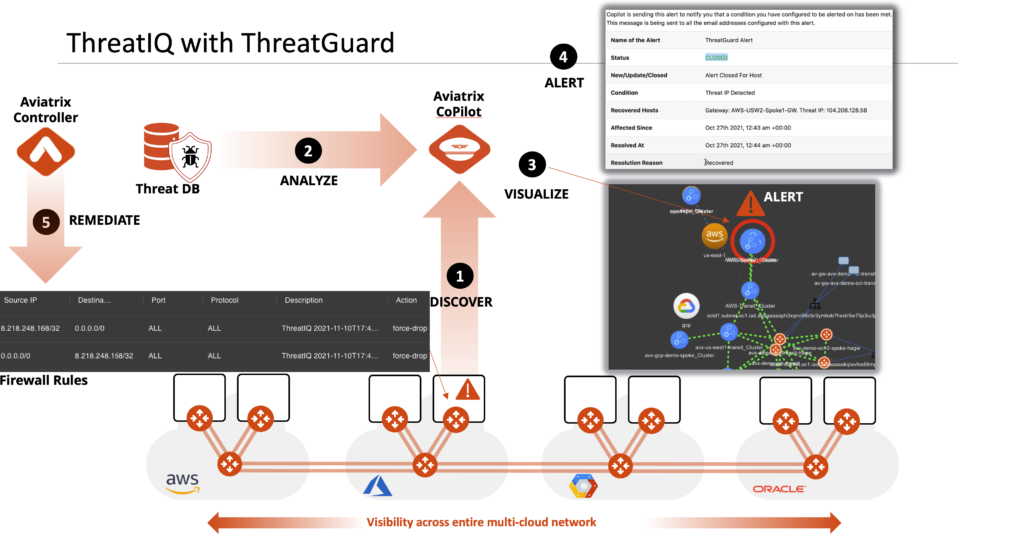
- The network feeds CoPilot with Netflow data to give clients the rich visualization they need to operate enterprise-grade cloud networks.
- CoPilot correlates this information with external malicious IP databases looking for matches
- Matches can be visualized and checked in CoPilot
- Alerts are created by CoPilot to be sent to backend systems
- The Aviatrix controller remediates the problem by creating a stateful firewall policy on the gateway most appropriate to block the threat
So, this was just a quick overview of ThreatIQ and ThreatGuard. However, I hope it’s clear now the risks that we are mitigating.
Once again, and I hope this is clear in my posts: I believe that security is a discipline and not a product. Security in layers is a critical approach to maximizing your business’s data protection, service availability, and online reputation.
Good luck out there and tune in next time for #4.



