I’ve been asked a number of times over the past few months about the Aviatrix Security Features built into our Secure Cloud Networking Platform.
As customers move and deploy workloads in the cloud, Security can risk being an afterthought or an element that can slow down developers (hence so many “workarounds”).
The driver behind this is a realization that certain (not all) Cloud-Native functions are still not at the level Enterprises require in order to remain compliant or meet their internal CISO/InfoSec requirements or regulatory responsibilities.
At Aviatrix, our mission is to bring enterprise-grade security features to the Cloud in a repeatable, programmable way that does not impact agility or developer experience nor compromise on your regulatory and security responsibilities.

I’ll be covering my Top 5 Security features over the comings days and weeks:
- FireNet
- High-Performance Encryption
- ThreatIQ and ThreatGuard
- Multi-Cloud Network Segmentation
- FQDN Filtering
1. Security Feature #1 – FireNet
Traffic flows require inspection at some point.
Enterprises need to secure, monitor and log traffic as it flows between application or BU boundaries (East / West), exits to the internet (Egress), enters from the internet (Ingress), or moves between the Cloud and external resources (North / South).
But where do you “insert” these firewalls? And HOW do you insert these firewalls in the Cloud?
Solution 1 – Use the Cloud Native Security Constructs
This could be as simple as leveraging Security Groups, NACLS (Network Access Control Lists) as well as their various equivalents across the major CSPs. But, without a centralized management point, a single source of truth, and comparable constructs across all Clouds, this quickly becomes a nightmare to operate and manage. You could leverage the AWS or Azure Firewalls, but these too are not repeatable across Clouds, still don’t offer parity with the NGFW (Next Generation Firewall) vendors, and bring a new kind of complexity to firewall management.
Solution 2 – Use NGFWs with Native Cloud Networking Constructs
The best is to take the NGFW vendor of choice, the one your CISO trusts, your ops team knows inside out and your regulators are on board with, and somehow jam it into the cloud. “Jam it in to the Cloud” is a technical term when dealing with Cloud Native Networking Constructs 🙂 It means figuring out how to service chain complex flows repeatably in any cloud, gain visibility, document it, and operate it (something Aviatrix do well :)).
This is where this falls apart. Not to pick on Palo Alto, actually one of my favorite Security vendors, but the complexity comes not in the Firewall itself, but in the service chaining and architectural design:
This challenge is the same no matter which firewall vendor you choose. Again, the challenge is inserting the firewall into the traffic flow in a manageable and repeatable way in any Cloud.
Solution 3 – Aviatrix FireNet
FireNet is a fully managed and orchestrated architecture and workflow for the deployment, insertion, and base configuration of NGFWs in the Cloud, in any Cloud.
We manage the, resilient and redundant, deployment of the NGFW VMs, and programming of NGFW, Aviatrix and cloud native routing to mark according to policy and push traffic to be inspected to the Firewall.
That’s a mouthful. Simply speaking, you define in the Aviatrix controller the policy specifying the traffic to be sent to the firewall, and the Aviatrix controller takes care of everything else. Any Cloud. Traffic not marked for inspection does not need to transit the firewall.
All the Security Team needs to do is push the Firewall Policy and manage the firewalls the same way they did before. Operational continuity, reduced complexity, easier troubleshooting and clear visibility.
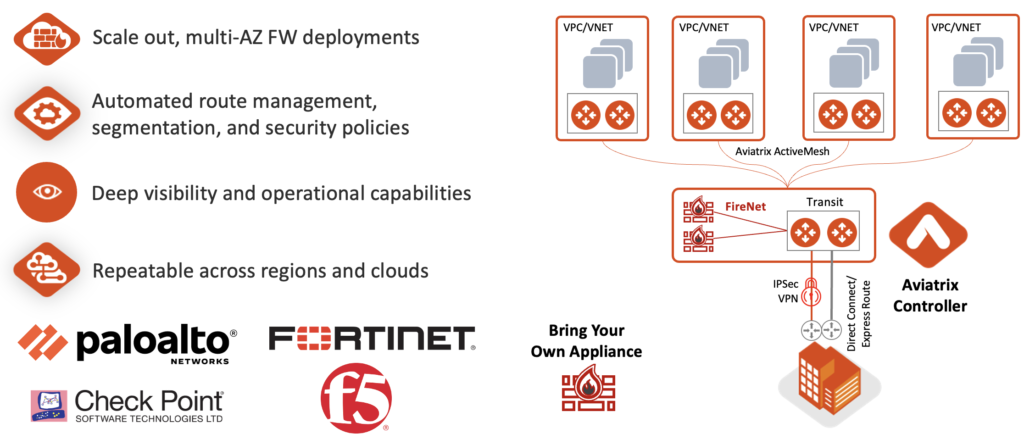
We support Palo Alto, Fortinet, and Checkpoint in a truly integrated way (we speck API directly with them to facilitate bootstrapping, route table management, etc) and other third-party devices on a case-by-case basis.
- But what about performance? Well, we can scale these firewalls horizontally and have been known to push around 75Gbps of throughput in some cases.
- But what about resiliency? We take care of AZ positioning and monitoring of both Aviatrix Gateway and Firewall health to redirect traffic flows around failed devices.
- But what about Mutli-Cloud? We have the same repeatable architecture in all the major CSPs – reach out to us for more details.
- But what about Infrastructure as Code? We support the full deployment of FireNet using Terraform.
Check in next time for High Performance Encryption…
In the meantime, here are some great links from colleagues on FireNet. Big shout out to Tim McConnaughy (https://carpe-dmvpn.com/about-me/) and Ricardo Trentin (https://rtrentinsworld.com/about-me/)



