Welcome to the 4th installment of my Top 5 Aviatrix Security Features.
If you missed them, you’ll find parts 1,2 and 3 here below:
But let’s kick things off with today’s topic, Multi-Cloud Network Segmentation.
What is Network Segmentation?
When we build out a network, our objective is to interconnect business intelligence and applications with the different stakeholders requiring access.
However, just allowing everything to access everything is not a good idea. Think of an airport analogy. The goal is to give passengers access to their outbound flights or ferry inbound passengers to their connecting flights or exit the airport. However, in order to make an airport function, there are numerous elements required. These elements have pre-defined roles and responsibilities and with it certain access rights, all enforced by a system of security controls.
Likewise, in an enterprise network, the underlying infrastructure must allow for the segmentation of different business processes/applications/environments to ensure the integrity of the applications, the resilience of the business, and the security of the data in question.
How do I segment?
In order to segment, a complete understanding of the enterprise applications, environments, and services is required. We begin by identifying groups of services that serve a common purpose or fit a common security profile.
These can be development environments (Production, Dev, UAT), production applications (BU1, BU2), application functions (frontend, application), or security environments (DMZ1, DMZ2).
Once we have identified these groups, the second part is the policy definition. Here there are various types:
- Black and white policy – no connection between segments
- Black, white, grey policy – no connection between certain segments, but allow connections to shared segments
- Inspection policies – segments may speak to each other, but not before passing an inspection policy (firewall type policy)
How hard can that be?
In the on-premises world, not hard at all. We’ve been doing it for years.
However, when you move to the Cloud – very hard indeed.
Why is that? Great question – it has to do with the diversity and limitations of the Cloud Native constructs at your disposal. You have elements such as Security Groups, Route Tables, Routing Constructs, that can all be complexly built to allow you to achieve some sort of segmentation within a particular Cloud Provider. It’s not pretty, but you could potentially do it at great development and operational cost.
The challenge comes with carrying this segmentation “policy” through to another CSP. This is where your “not-so-pretty” design just gets plain ugly.
So, what’s needed?
We need a common data plane and control plane within the CSP and across all your public CSPs so we have a common enforcement point for the classification of traffic and the enforcement of the policy.
Lucky for us, Aviatrix provides just such a solution:

As you deploy your business workloads in different VPCs, VNETs, VCNs, etc, our architecture gives you the consistent data plane that interconnects everyone.
But that may not always be the desired behaviour.
We, therefore, offer the ability to identify groups of workloads that share a common use:
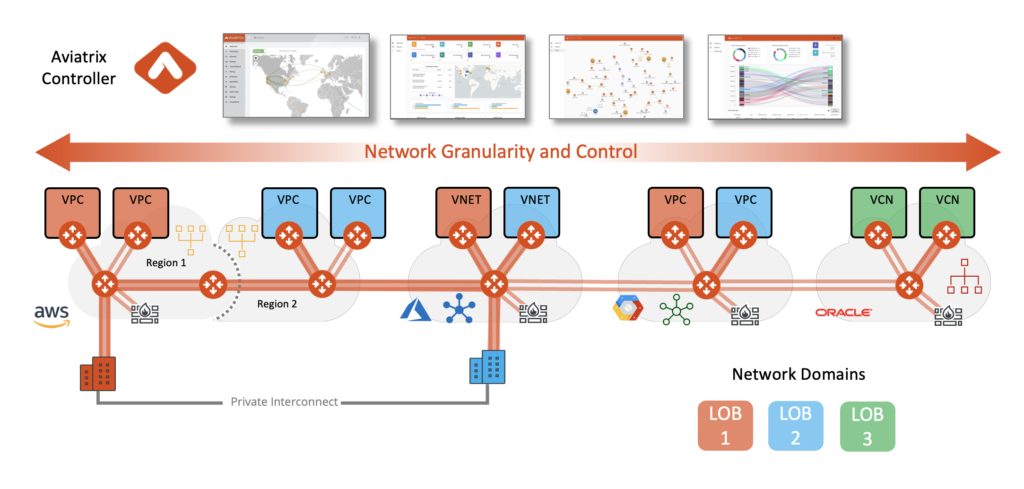
As you can see from the above graphic, we do this at the VPC level or external attachment level.
We refer to this as Macro-Segmentation.
Our policy can then be written referencing the “orange” group or the “blue” group and defining who can and cannot speak to each other.
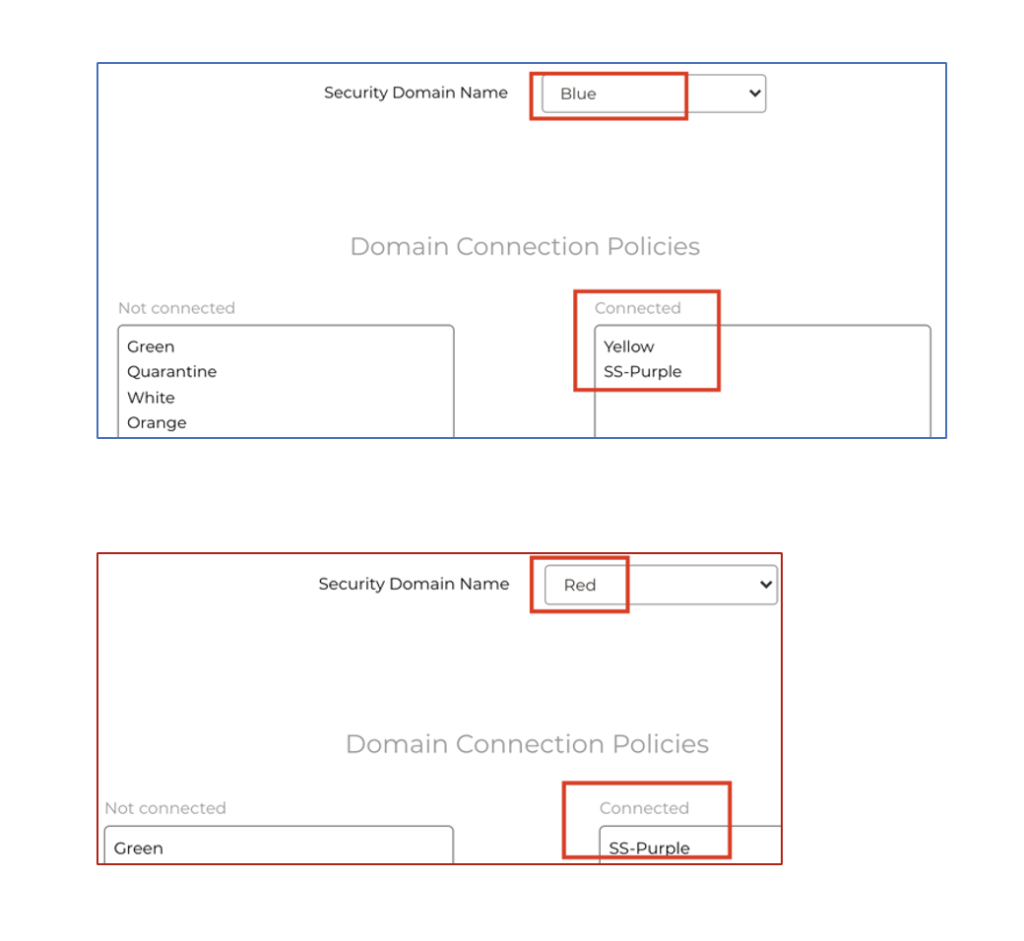
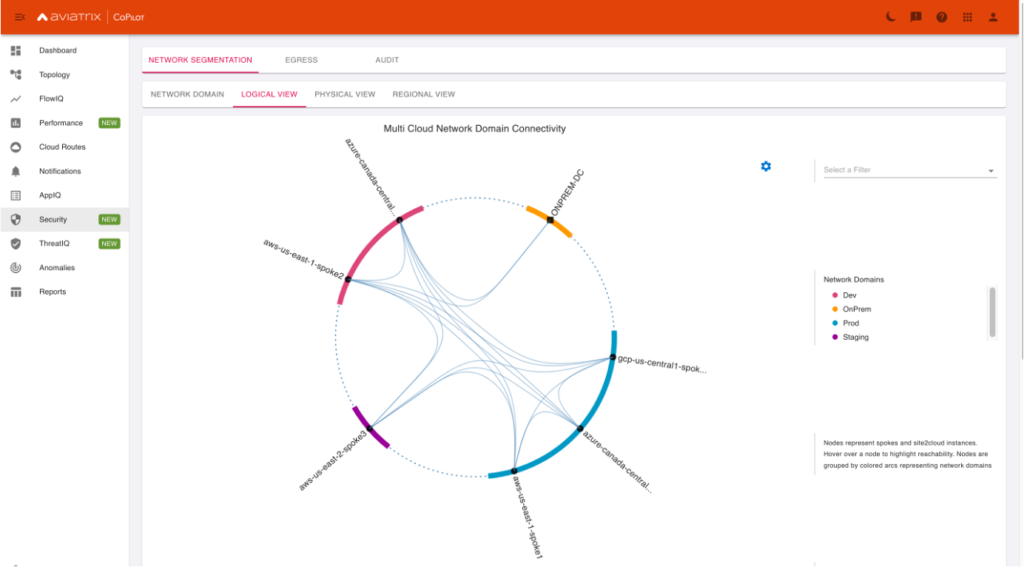
This can all be easily viewed in CoPilot:
Great, but I need more granular segmentation than that.
Thought you might.
That’s why we also support Micro-Segmentation.
We now allow for the identification and grouping of applications within a VPC into what we refer to as Application Domains:
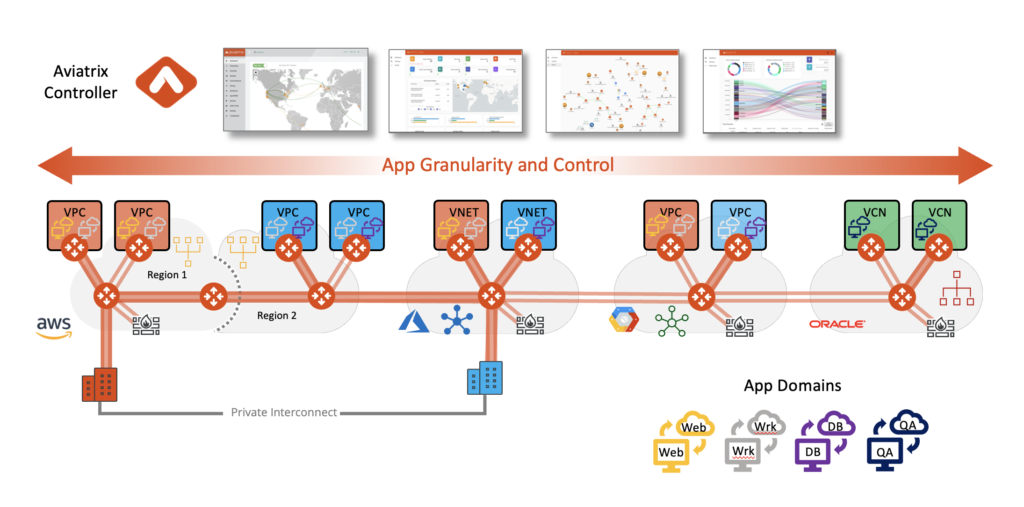
Now your policies can be even more granular meeting your security and business needs.
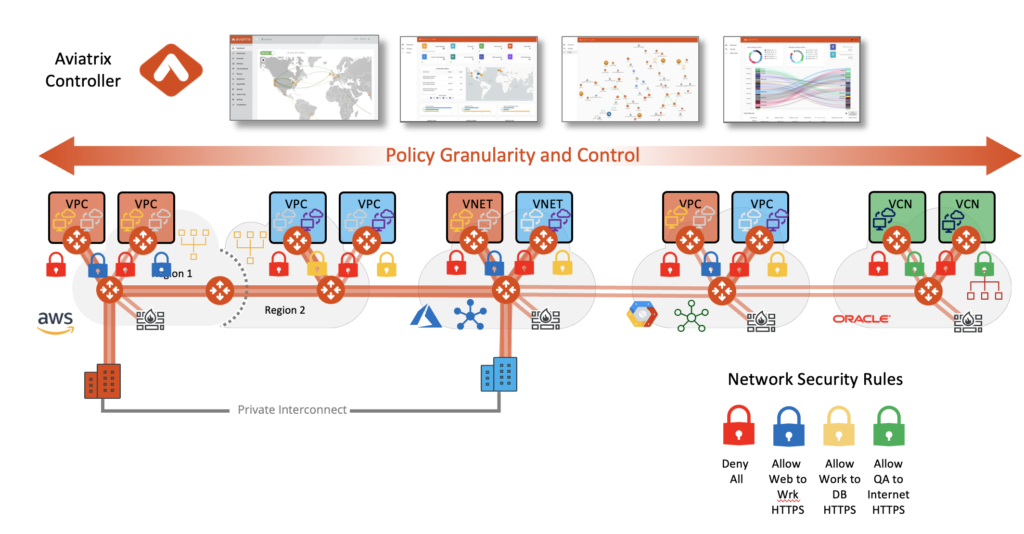
As you can see, we can now begin to enforce policies that would previously require a firewall in the chain.
With this approach, we increase performance and potentially cut down on cost.
Conclusion
I hope you retain the following from this post:
- Network segmentation is important
- Network segmentation in the Cloud is hard
- Network segmentation across Clouds is much harder
- Aviatrix greatly simplifies the enforcement of network and application segmentation policies
But don’t take my word for it. Reach out for a design discussion and demo.
Check in next time for the next installment.
Thanks for reading.



