This post addresses micro-segmentation of traffic flows in the cloud to enforce a predefined security policy.
When watching any Tech video from Aviatrix, this functionality is always called out, but in my opinion it is sometimes brushed over quite quickly. I think it’s worth a closer look.
The great thing about this feature is that you don’t need any extra security devices to deploy it. If you are running Aviatrix as transit in the Cloud, you have this functionality as default.
In case you missed my posts on building an Aviatrix lab using Terraform you can find part 1 and part 2 by clicking on the links.
What are we building today?
As a reminder, here is the infrastructure we built in Part 2:
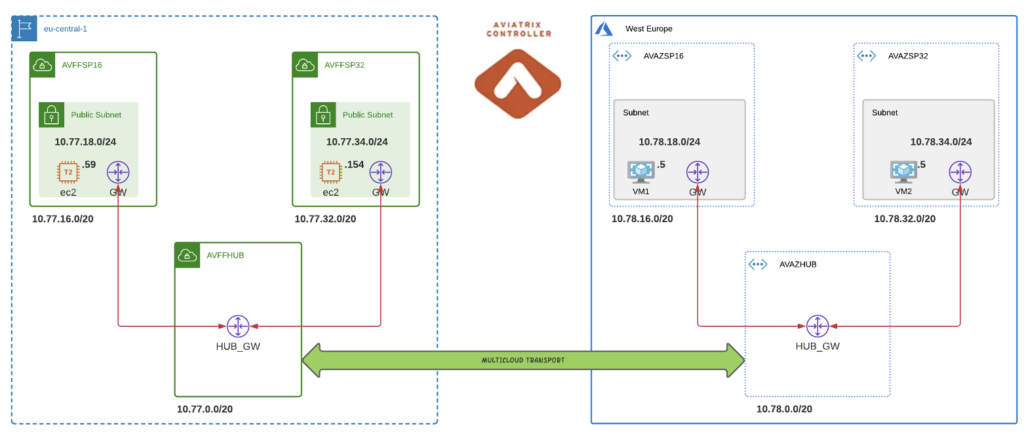
Let’s talk about micro-segmentation.
We want to split our infrastructure into security domains and then define a policy as to which domains can communicate. Straight forward.
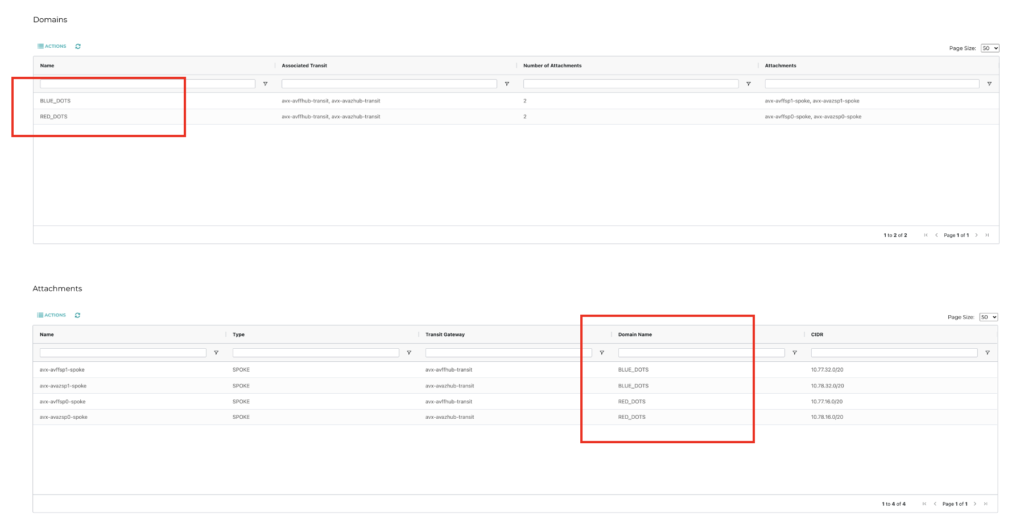
What we want to achieve is the below. We designate certain VPCs as belonging to a particular Security Domain.
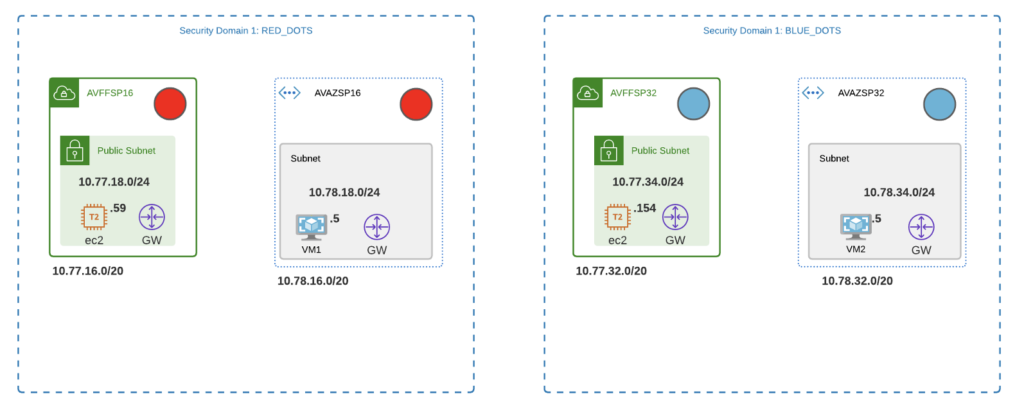
In this case, the RED_DOTS and the BLUE_DOTS.
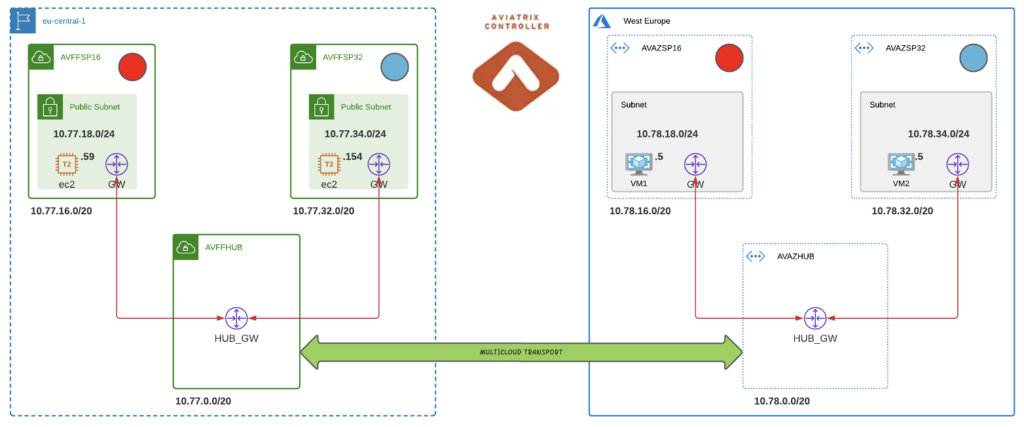
This allows us to define a Policy to enforce certain rules. In the case below I would like to allow the BLUE_DOTS to speak only to other BLUE_DOTS and likewise for the RED_DOTS to speak only to RED_DOTS.
BLUE and RED must never speak to each other:
Before we go any further, let’s verify our default connectivity (before segmentation and policy enforcement):
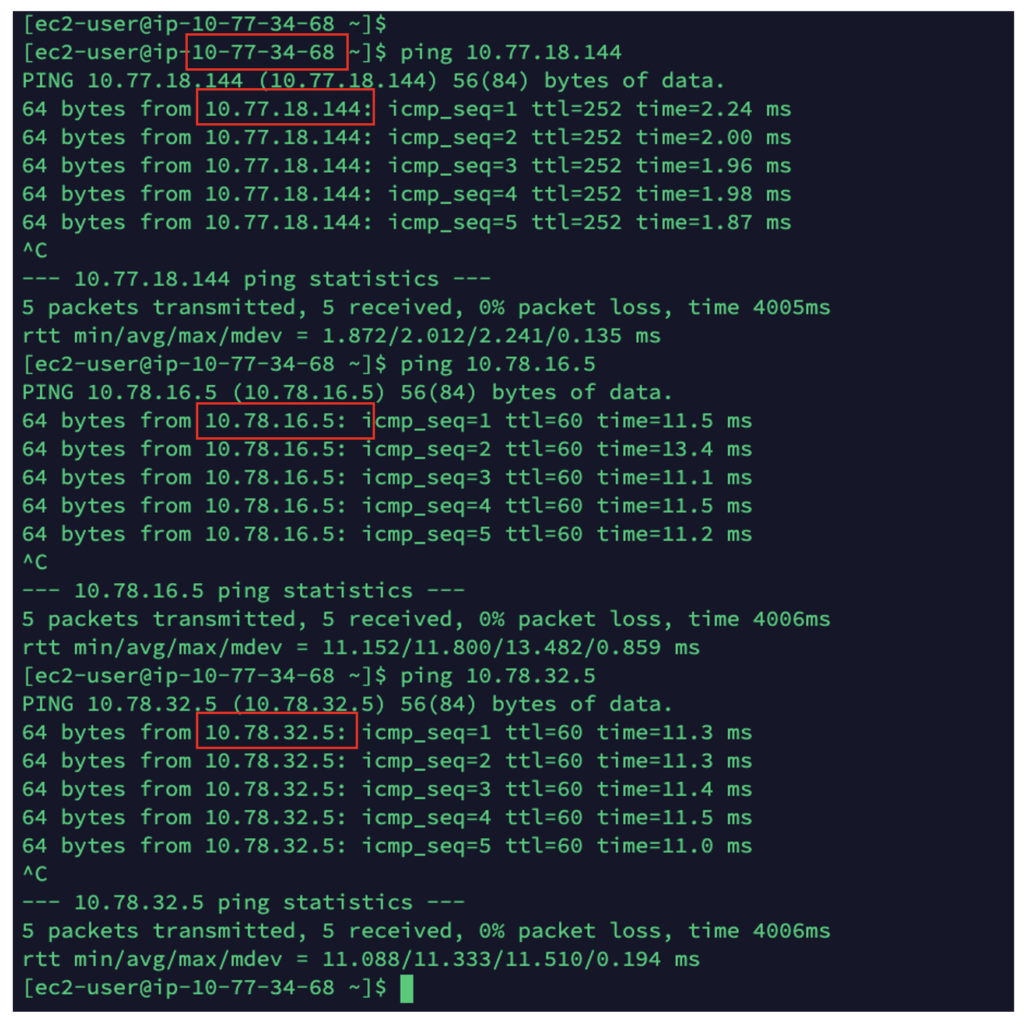
As you can see we can reach everything.
Get Micro-Segmenting!
We start by going to the controller:
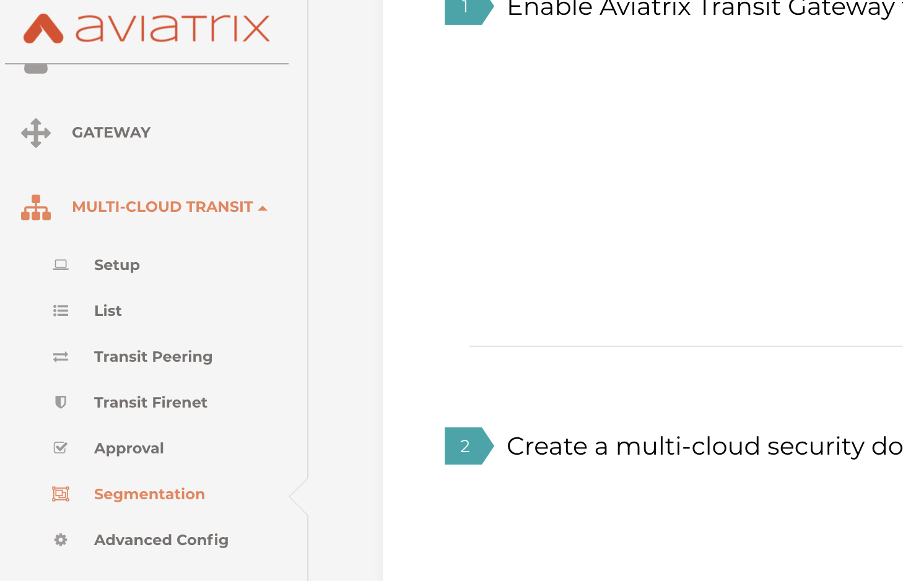
Step 1 is to enable the transit routers and create the Security Domains.
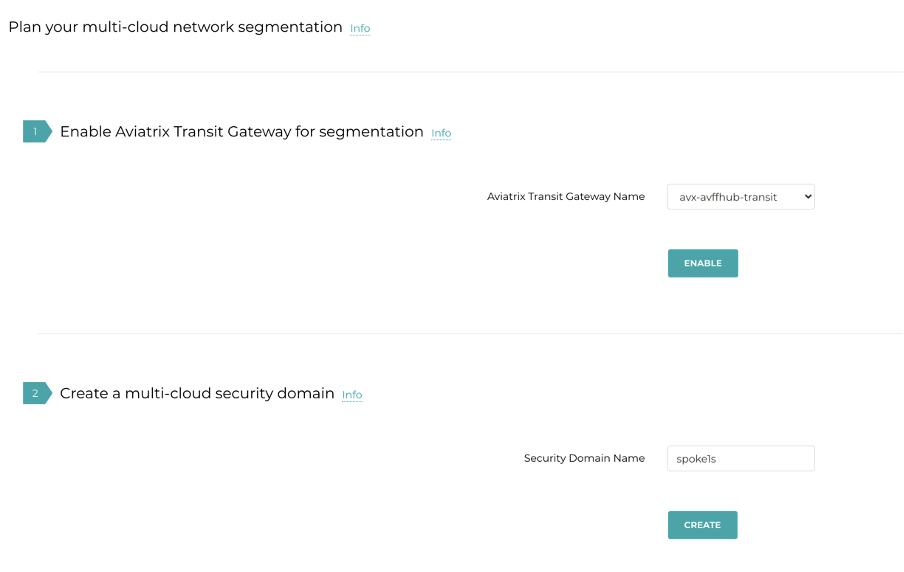
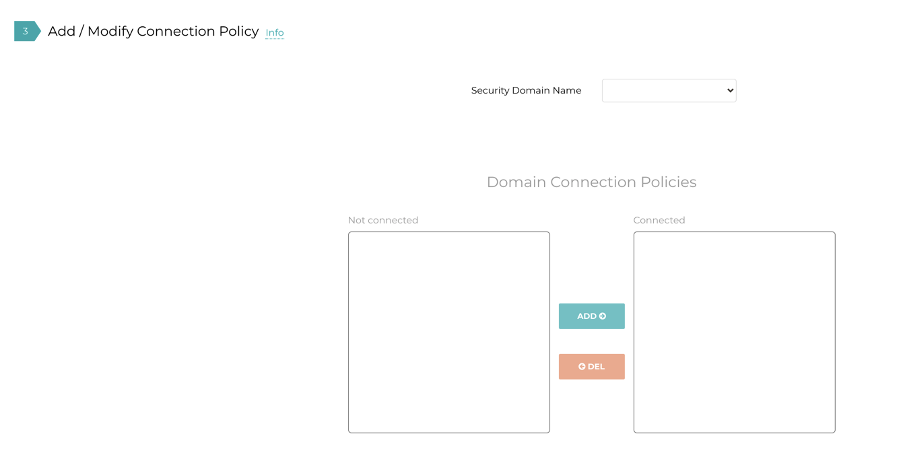
There is a section 3 here, but let’s ignore it for the moment.
Step 2 is where we associate the Security Domains to the gateways in question.
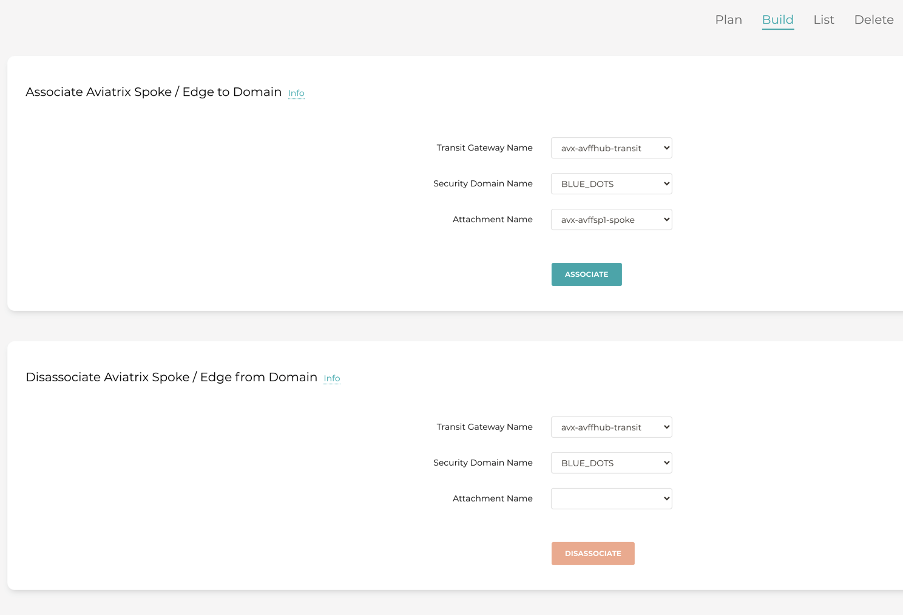
Step 3 is verification.
Let’s check the connectivity
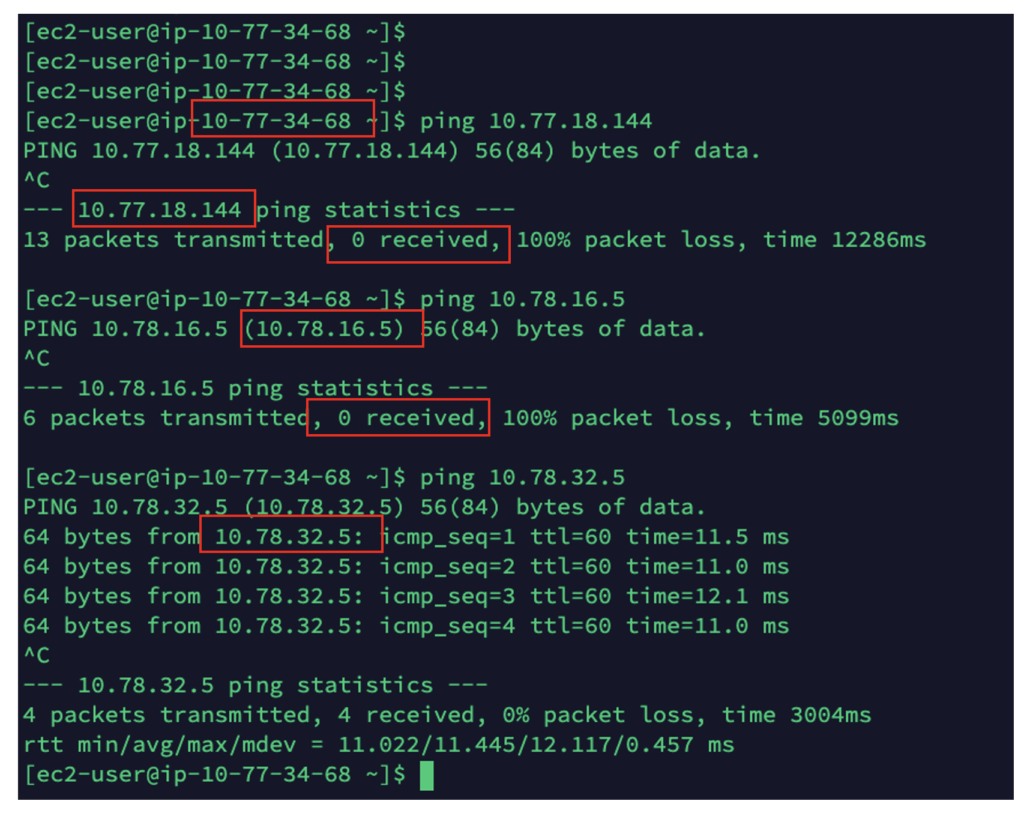
As you can see, my connectivity is limited to the other endpoint in the same Security Domain. I cannot reach endpoints in another Security Domain.
Policy Modification
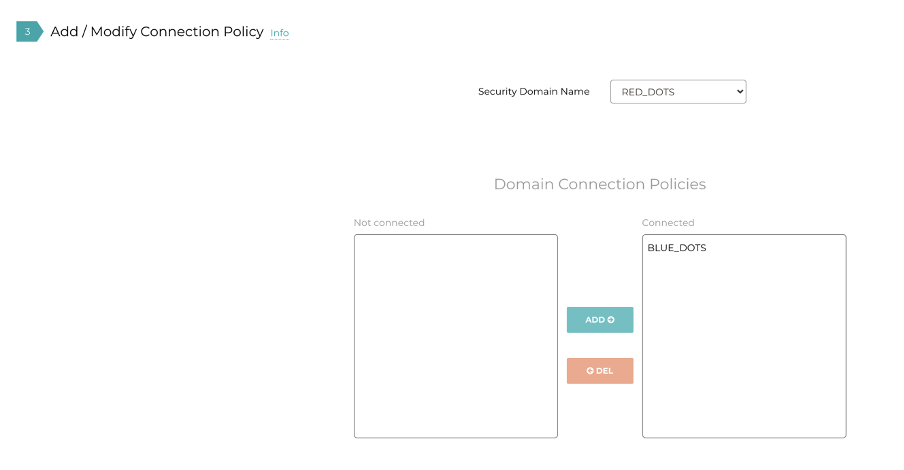
Now, let’s have a look at the “Plan” tab, section 3 again (the one I said to ignore before).
In this section we can add a Connection Policy to allow the BLUE_DOTS to speak to the RED_DOTS:
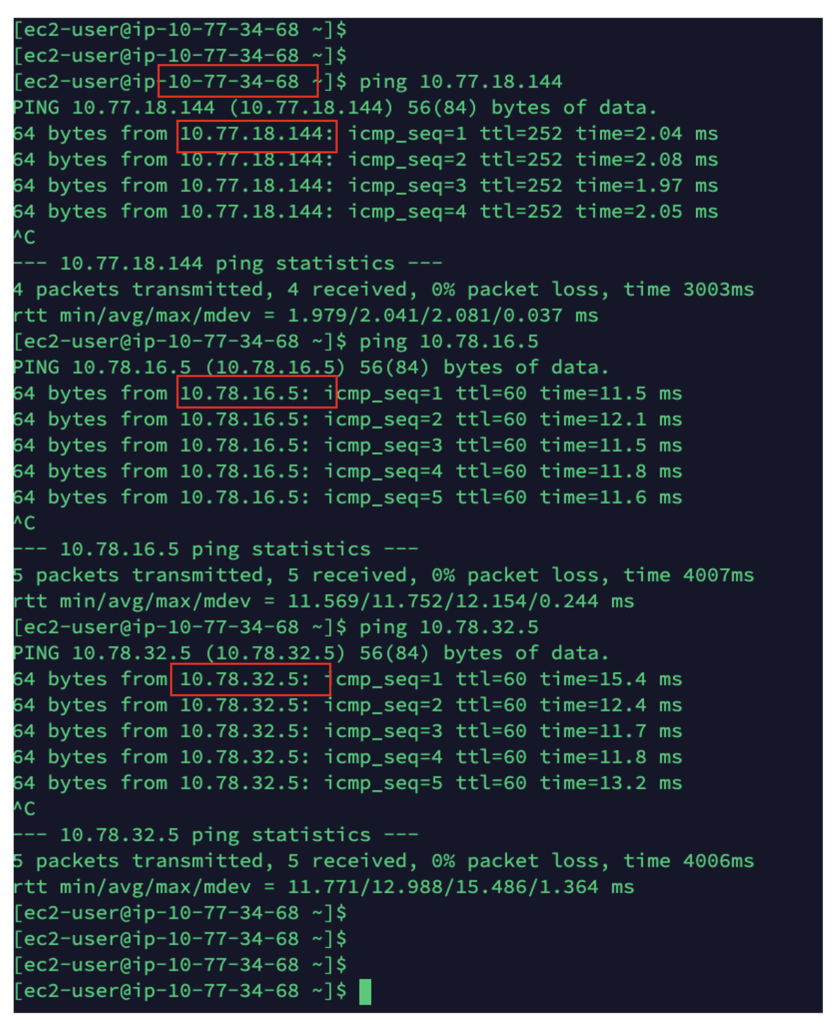
After modifying the policy, we can now ping between the security domains as before:
So, that’s it for today. A short post, but an important one.
Let me know if these are useful or if there is any specific content you would like me to create.
Thanks for reading.



